
Data Leak Visibility
In my last post Limitations of Data Loss Prevention Solution, in the conclusion, I mentioned that osquery is a formidable open source agent for endpoint visibility on most common operating systems such as Windows, macOS and Linux. It can provide an audit trail for user actions. It exposes operating system and events on the system as a high-performance relational database. The osquery agent can be deployed as a standalone package which can run as an application or daemon/service. Typically, in an enterprise deployment you would want it to run as a daemon on *nix machine or a SYSTEM level service on windows.
Having an agent on an endpoint is obviously not enough, you also need something to manage those agents. This is where open source really shines. There is an open source manager just for this purpose called Kolide Fleet, which connects agents and allows admin to query any agent(s) for specific information from their host(s). Because osquery natively exposes the OS information as a relational database, there are many tables and each table can be queried using SQL query directly from the Kolide Fleet manager.
There are number of ways to deploy the Kolide Fleet manager, such as an on-prem server running the Kolide stack or a cloud deployment with instances running the Kolide stack components. For most enterprises, a cloud deployment would be a cost-effective and expedient way to try out Kolide Fleet manager and learn the capabilities for osquery. The developers of osquery and Kolide Fleet (one and the same) have done excellent work in making both open source and provide solid documentation. In addition to this, there is a large open source community supporting both. Many large enterprises continue to add additional features and functionality, which makes it a viable solution for endpoint visibility for small or large enterprise.
Endpoint Fleet Management
I wanted to demonstrate the power of cloud deployment, the ease with which I was able to get my system up and running and put my AWS learning to good use. I created the architecture shown below for a cloud deployment of Kolide Fleet Manager.
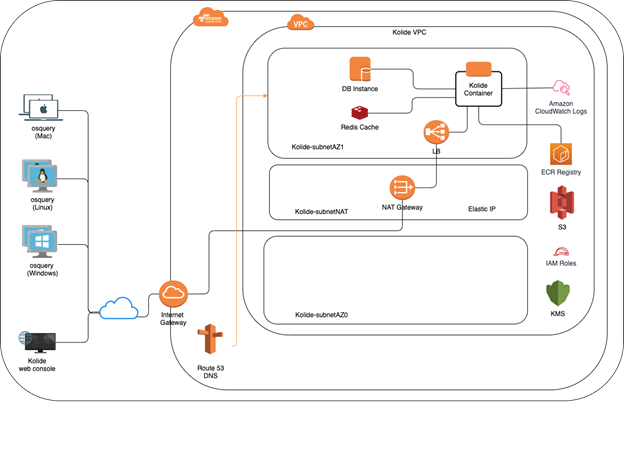
The magic of infrastructure as code is awesome!
I was able to create the complete system using a few YAML templates in AWS Cloud Formation. I can create and destroy the complete infrastructure at will within a few minutes.
The interesting challenge in creating this architecture was using a domain I purchased through GoDaddy and route traffic using AWS Route 53 DNS to my Kolide stack.
I also felt that somehow AWS should provide the capability to create the infrastructure diagram automatically based on the connected components. Hopefully, an AWS product manager reads this blog.
Endpoints Visibility using osquery
I created four endpoints in my home network (Windows 10 VM, Linux CentOS 7.2 VM, macOS 10.15 and macOS 10.14) installed osquery on them and connected them to my cloud deployment. The reason I wanted to create two macOS endpoints was to see how well osquery works on macOS 10.15. One of the challenges for such agents is that Apple has introduced significant security restrictions for applications, and I wanted to observe if there were any potential issues running osquery on macOS 10.15. I did not observe any issues in my tests.
As it can be seen below the home page displays the endpoint machines.
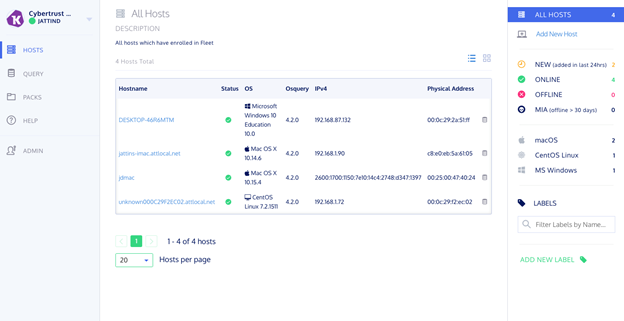
When the endpoints are disconnected, their status will change from online (green) to offline (red). As more endpoints are added they will show up as new hosts in the home page. It also displays the OS type and versions which is very useful if you need to ensure compliance.
Data Leak Information
I will not go into each of the tables and queries supported by osquery as the documentation provided by osquery docs does an excellent job, instead I wanted to focus on the usability of such a system in a typical enterprise environment for Data Leak Information (DLI). There are three use cases I was able to easily verify for DLI on macOS:
- Capture information on documents printed from a host. On macOS, the printing uses CUPS (Common Unix Printing System) and osquery has a CUPS table which will capture any documents being printed from that host. This indeed is very helpful where one needs to capture potential data theft.
Using a simple SQL query shown below, I was able to a get a complete list of every document ever printed from my machine (all records dating back to 2014 and well before I installed osquery).
SELECT * FROM cups_jobs;

The image above is from the exported csv file from Kolide Manager and shows the various times in Epoch time. The Epoch time (1598384396) translated to human readable date/time for the Financial Data – Confidential.pdf is Tuesday, August 25, 2020 12:39:56 PM GMT-07:00 DST. It also shows the username of the individual who printed the document.
- Capture information on documents being copied to a USB device on a macOS host
- Capture information on documents being copied to a share drive from a macOS host
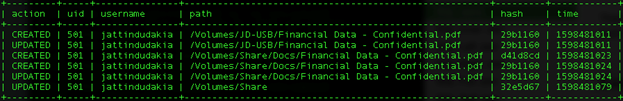
Using the following somewhat more complex SQL query shown below, I was able to a get information on documents copied to both USB and network share drives.
SELECT action, file_events.uid, users.username, SUBSTR(target_path, 1) AS path, SUBSTR(md5, 0, 8) AS hash, time FROM file_events INNER JOIN users ON file_events.uid=users.uid WHERE sha1 <> '' AND target_path NOT LIKE '%DS_Store';
The results of running the query locally will show all files copied by a user to either a USB or a share drive as shown below.
Conclusions
There are several large enterprises using osquery for different use cases such as monitoring, incident response, IT compliance and vulnerability management. For each of these use cases, osquey supports a configuration through packs (groups of predefined quires, which run on a pre-defined schedule). I have presented yet another use case which osquery can easily support for monitoring DLI.
In a typical enterprise environment, it is unrealistic to query each of the hosts, but the capabilities built into osquery allow it to be connected to an ELK stack or to AWS Kinesis. The data gathered from all the hosts can easily be analyzed for such leaks. This makes an osquery based fleet very powerful for monitoring systems across the whole enterprise.
